Protecting Your SACCO's Financial Ecosystem.
Why Kwara is the unparalleled choice for SACCOs seeking top-notch security.
Keeping your data safe, every step of the way.
Your financial information is both personal and powerful — that’s why security is a top priority when we're designing our products, policies, and practices.
Modern Technologies
We always keep our technology up to date with the most advanced security measures, such HTTPS, XSS prevention
Secure Policies
Our products prioritise secure policies such as least-privilege, data encryption in transit & at rest and secure-by-default
Independent Security Testing
We invest in regular security reviews and pen-testing to keep ahead of any new vulnerabilities known to the cybersecurity sector
In-built Access Controls
We have ensured that SACCO admins can track and secure access controls with maker-checker, password resets & 2FA, forensic audit trails and log-in trails
Useful tools to protect your data
Our information security program is designed to meet or exceed industry standards, and we use many different controls to keep your personal information safe.
Verified partners and compliance certifications
Security comes first at Kwara. We use the world’s best in class hosting with AWS and ensure at least one serving copy of the data may be stored in a data centre located in Kenya.








Frequently Asked Questions
Does the system have an audit trail?
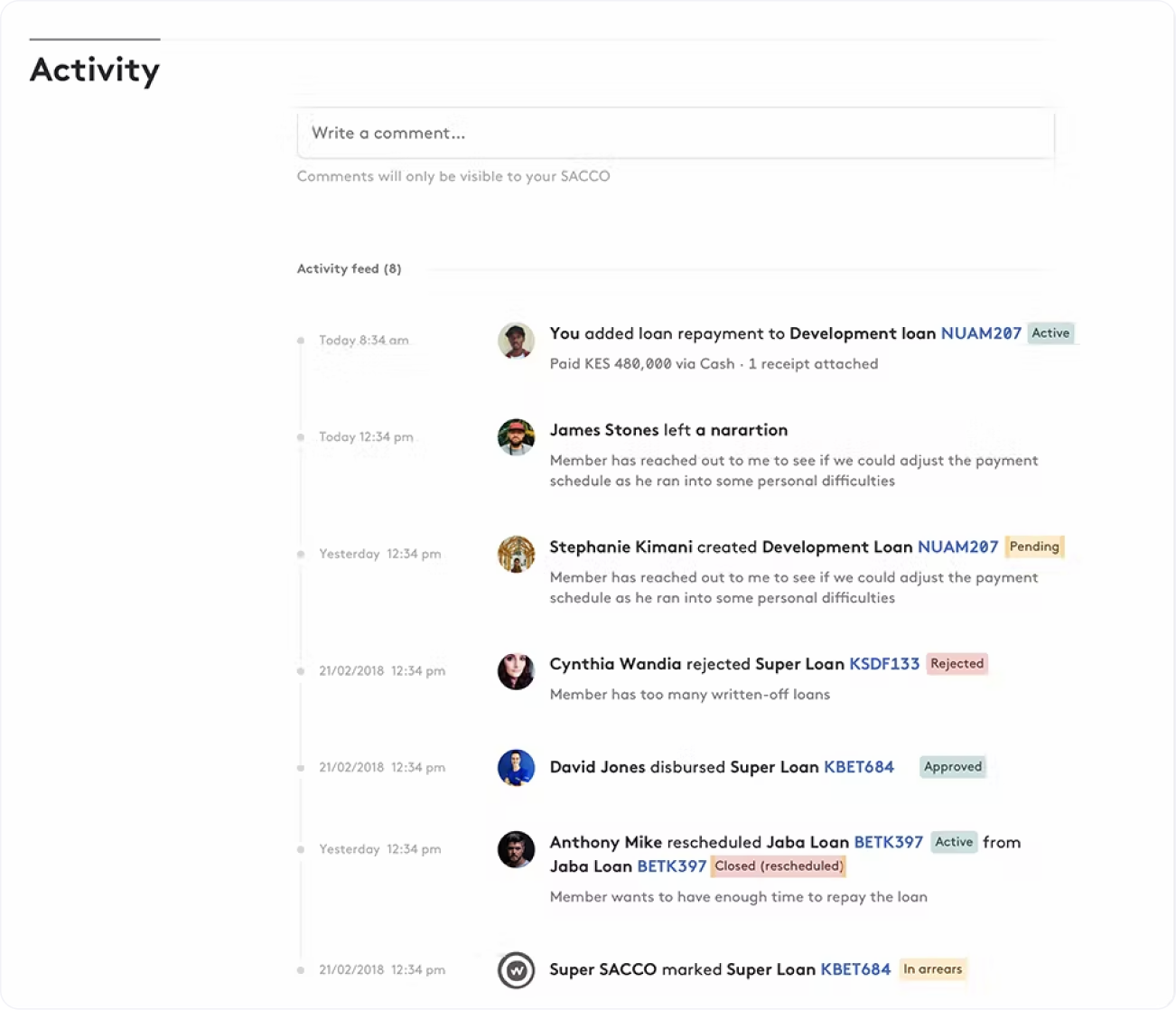
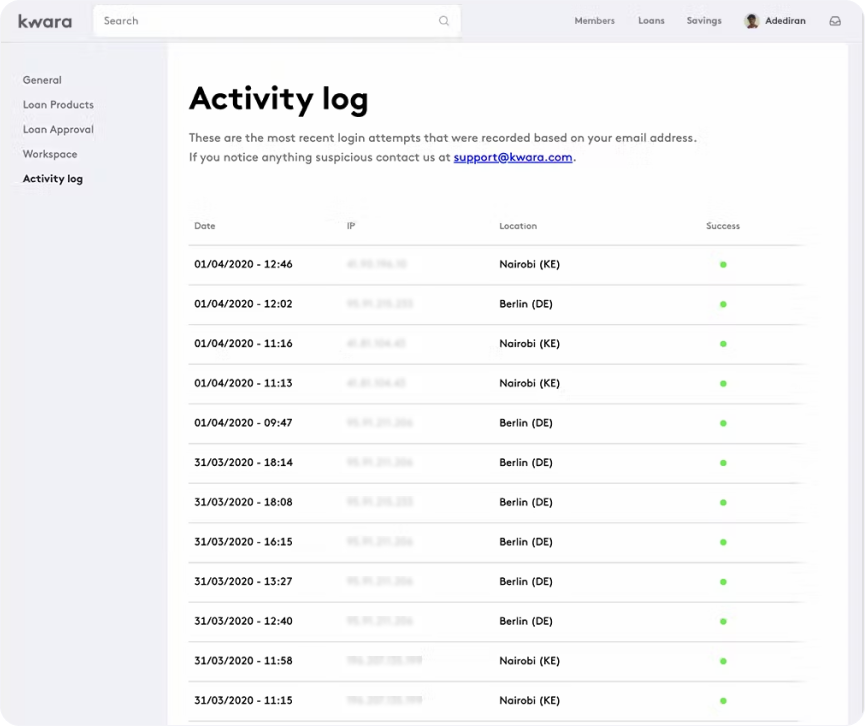
Yes! There is a live activity feed that allows the system administrator to view in detail all activities on the platform. This allows for detailed forensic audits that can retrieve historical information including date and time, transaction type, creator of transaction and the nature of the transaction. The audit logs are immutable and are generated automatically as actions are created. This creates an automated monitoring system directly within the core banking system that cannot be tampered with.
What are your maker checker controls?
All transactions happen within workflows that have defined stages for input and approvals. Roles are created and granular permissions assigned (View, Create, Delete, Approve) according to the user’s role within your organization.
How do you monitor and guard against common attacks?
We have multi-pronged approach for security, including firewalls in place for all our web applications. The firewalls apply OWASP recommended rules in order to guard against attacks. We also deploy several proprietary programs to mitigate against brute-force attacks.
Is the system web-based, cloud based or desktop based?
Kwara is web and cloud-based.


